OUR SOLUTION FRAMEWORK, METHODOLOGY & CASE STUDIES
Guiding Principles
01
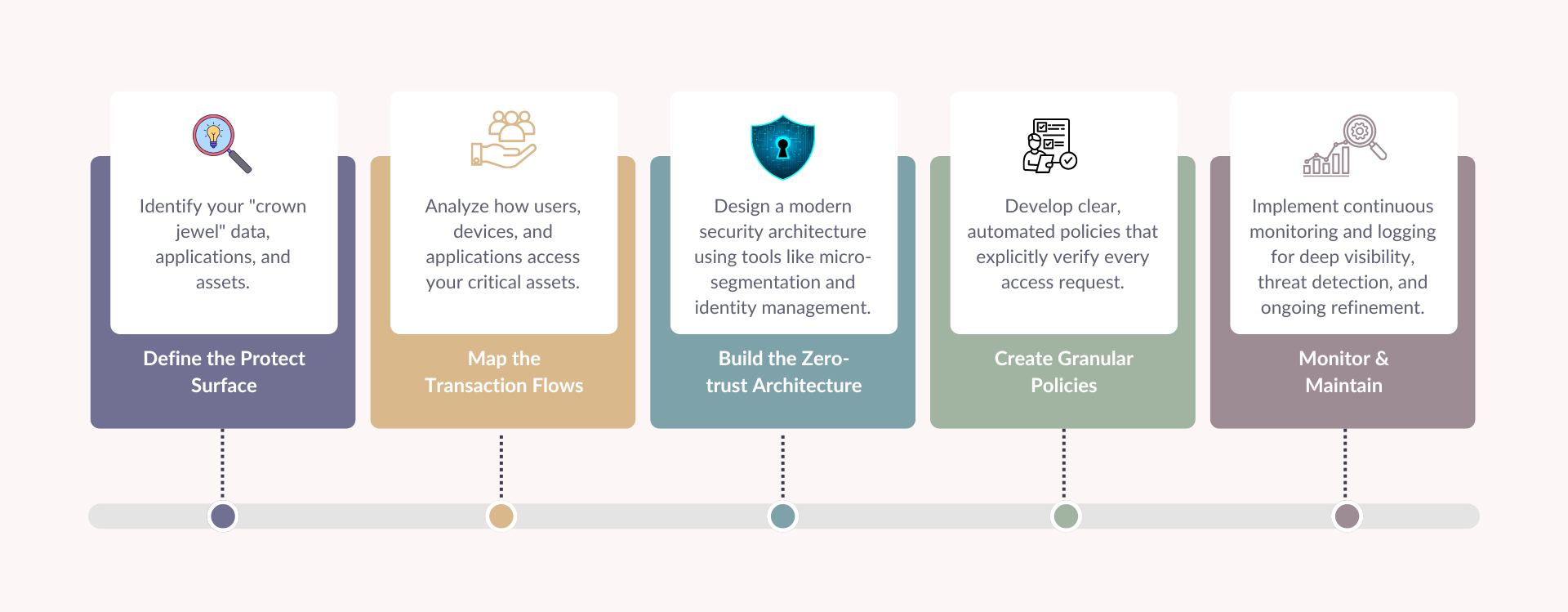
Secure the Mission
We begin by understanding your business and prioritizing the protection of your critical assets to support your mission.
02
Verify Explicitly
Trust is not assumed. Each user, device, and access request is explicitly verified, removing implicit trust from your environment.
03
Defend from within
Security is essential for your data. We create controls that safeguard your information wherever it travels.
04
Adapt Continuously
The threat landscape and defenses are constantly evolving. We implement continuous monitoring and improvement to keep your security effective.
Our 5 Steps
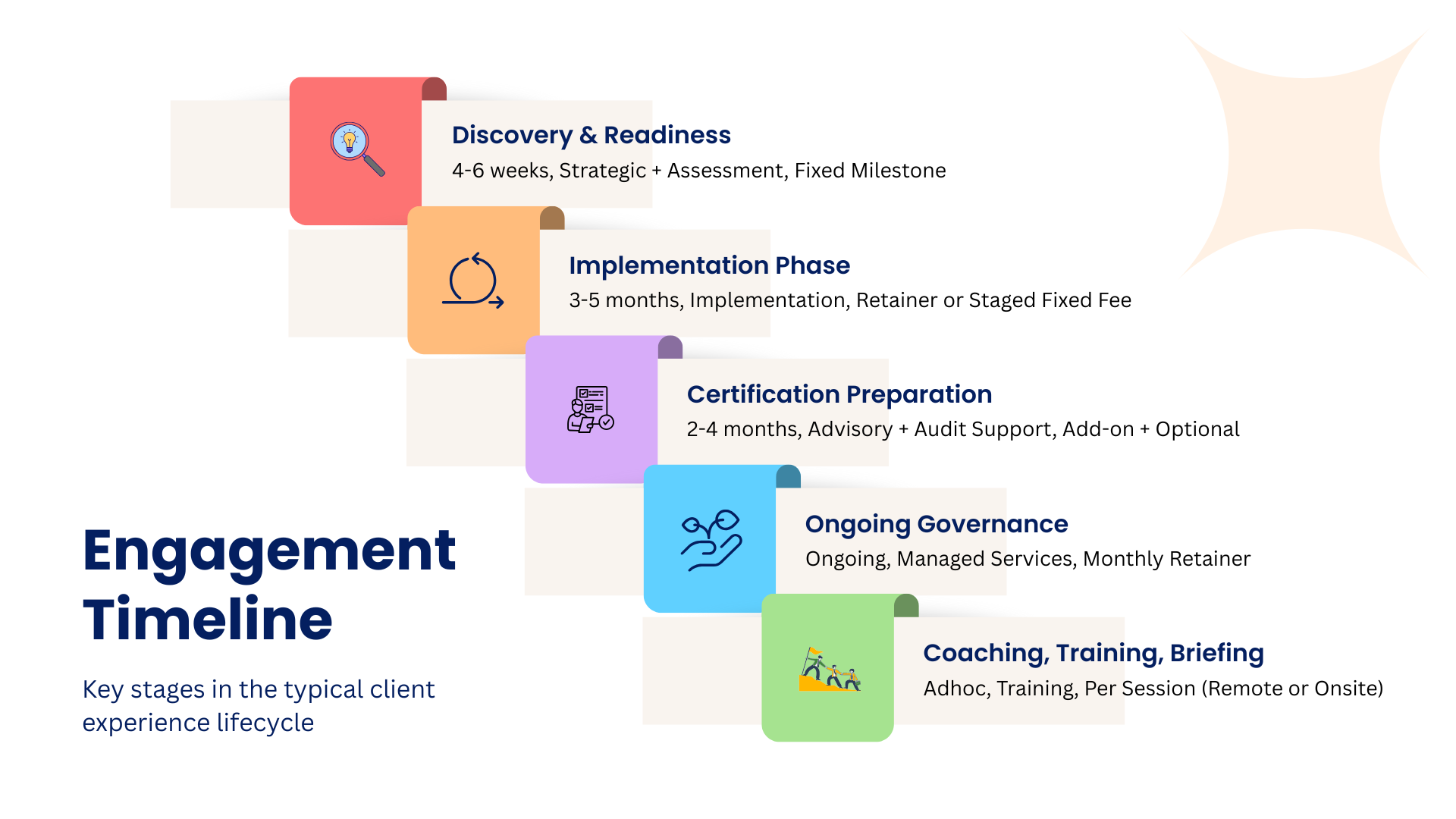
TYPICAL TIMELINE
CASE STUDIES
Unlock Our Blueprint for Success
Go beyond theory. We understand that every sector faces unique challenges.
Our case studies are detailed blueprints that reveal the exact strategies we've used to solve complex security and governance challenges for industry leaders. See the real-world results and discover the proven process you can apply to your own organization.
Go Beyond Theory
Our case studies are detailed blueprints that reveal the exact strategies we've used to solve complex security and governance challenges for industry leaders.
Law Firm
Challenge: Securely deployed Microsoft Copilot across the firm without compromising attorney-client privilege.
In this Case Study, You'll Learn: The 3 key policies we created to prevent AI-driven data leakage in a sensitive M365 environment.
Autonomous Systems & AI
Challenge: Achieved ISO 27001 & 42001 certification to win major enterprise and government contracts.
In this Case Study, You'll Learn: How we embedded a Hardware Root of Trust to secure their drone fleet from the ground up.
Accounting Services
Challenge: Eliminated a critical vulnerability by migrating sensitive financial data from insecure file shares to a fully governed cloud environment.
In this Case Study, You'll Learn: The automation strategy that cut their audit preparation time by over 70%.
Government Agency
Understand how we designed and deployed a cross-agency data sharing protocol that met strict federal security mandates.
Legal Firm
Zero Trust for M365 & Copilot Readiness

Challenge: A growing law firm was concerned about protecting sensitive client data in Microsoft 365, especially with plans to roll out AI tools like Copilot. They had no formal data classification and partners were using unapproved cloud services.
Results:
- Reduced data breach attack surface by over 60% by eliminating insecure network shares and unmanaged SaaS apps.
- Achieved 95% classification coverage for all attorney-client privileged documents.
- Blocked over 150 potential data leaks per month with new DLP policies.
Accounting Firm
Securing Financial Data & Automating Compliance

Challenge: An accounting firm struggled with securing sensitive audit work papers and client tax records. Their data was spread across insecure network drives and auditors occasionally used personal email, creating significant compliance risks.
Results:
- Automated data retention for over 10 million financial records, ensuring legal compliance.
- Centralized identity management for 20+ applications, eliminating weak access points.
- Provided a complete audit trail for all access to sensitive client data, simplifying compliance checks.
Drone Services
Achieving ISO 42001 AI Certification

Challenge: A cutting-edge drone service provider needed to build a secure and responsible AI management system to handle sensitive aerial data and achieve ISO 42001 certification.
Results:
- Successfully achieved ISO 42001 certification on the first attempt.
- Built a hardware root of trust into the drone fleet, ensuring data integrity from the point of capture.
- Provided full transparency and audit capability for all AI-driven decisions, building trust with clients and regulators.
HR
Protecting the Employee Data Lifecycle

Challenge: A corporate HR department was managing highly sensitive employee PII across a fragmented ecosystem of apps (Workday, iCIMS, Gmail) and a vulnerable on-prem payroll directory.
Results:
- Eliminated a critical vulnerability by decommissioning the insecure on-prem payroll share.
- Secured the full employee lifecycle, from recruitment in iCIMS to off-boarding in Workday.
- Enabled HR to safely handle PII while complying with privacy regulations like GDPR and CCPA.





